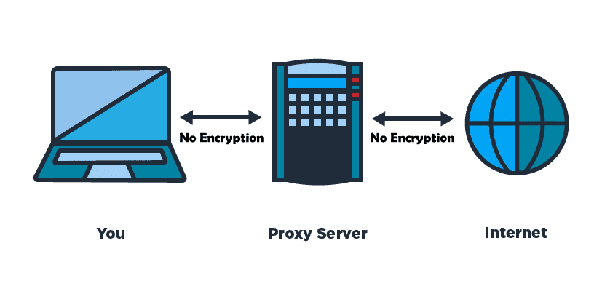
What is a proxy
Another computer that serves as a hub for the processing of Internet requests is a server. With these servers’ help, your computer sends your requests to the server. As a result, return your requests. It also intermediates your home machine with the rest of your internet computers in this way. On the other hand, people use these servers for various reasons. The reasons are filtering web content, controlling parental blocks, screening downloads and uploads. Furthermore, another reason is anonymizing internet visitors.
What is a proxy – a cheap proxy
Cheap proxies are agents which you can sell at a lower price than the average market. Yet, people should take this substandard alternative into account before purchasing these proxies. Resellers sell cheap proxies that do not have their own added value. That’s why you can not give any guarantee to these proxies’ stability. Besides, certain companies sell cheap proxies. They are never reliable about potential safety risks when using such proxies.
What is a proxy – how do proxy servers work
In its local archive of the previous pages, a server accepts a message for an Internet resource a Web site. If the website is available, return it to the user. So, the users can experience without distributing the application on the Internet. If the page is not in the cache, the service uses one of the user’s IP addresses as a client. So, the proxies ask for the web page from the server.
This server links the page back to the initial request and forwards it to the recipient. For legitimate and criminal reasons, you use such sort of servers. You can use a proxy server in the business for confidentiality, administrative monitoring. So, people use these servers.
This proxy helps user anonymity and anonymous navigation in the personal computing sense. Besides, the proxy server is solid to the user. All Internet requests and returned replies appear to the Internet server.
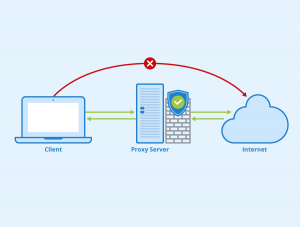
The server answers like the proxy are not invisible. So, it must state its IP address as a browser or protocol configuration option.) Users can use a proxy server to access online web proxies or customize web browsers.
Identified browser settings and HTTP, SSL, FTP, and SOCKS manual options provide browser settings. By the way, proxy servers may serve many users or only one per server. These alternatives are popular and committed proxies. Thus, a range of proxy server models exists, often in overlapping categories.
What is a proxy – uses
Proxies for personal use
Individuals or organizations may use a proxy for many reasons. If you need the proxy to access the Internet more, it may help daily Internet users. Besides the privacy aspect, proxy servers may enhance safety standards. When the proxy server configures, the users may encrypt their web queries. Also, you may do if the actual IP address does not have the right to access this specific material. A proxy attached to a particular position will disc lock geo-blocked content.
Proxies for business use
At the level of a company, the same conditions occur as before. Besides, companies use proxy servers by themselves to access and manage their Internet use. Most organizations use proxies to carry out their day-to-day tasks. In contrast, travel fare activities scrap airline rates without IP blocks or interdictions. You use a broker to access price details. So, buy items with limited editions. Furthermore, hand creates and maintains social media pages and many other purposes.
What is a proxy – need of a proxy server
It depends on your working if you need a proxy server. A VPN should be more than enough if it is to hide your IP address alone. You need a proxy server if you search for representatives. Also, the thing you need to collect is data in vast amounts. There are many proxies to bind to the requested data source.
I’m going to use your automated site scraping script for a larger web scraping project. You will collect the necessary data from the webserver. If you use proxies without exceeding the limits implied and slip under anti-scraping steps.
So, to respond if you need such a way? Yes. Yes, yes. You have, of course, to know the amount of knowledge you need. In other words, how many demands are you going to make every day? You should pick the best proxy for your specifications. And, this process depends on data points (or request volumes) and traffic.
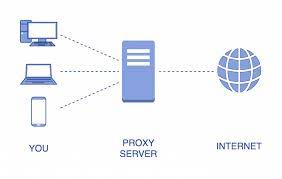
What is a proxy – Proxy hacking
With proxy hacking, the attacker intends to attack the search engine database index. They also attack search results pages of an original web page. The hacker will have a fraudulent website. This website emulates the original or whatever customers want to see on the page.
This proxy is how it functions. A server replica of the intended web page uses techniques. Furthermore, they are stuffing keywords to improve the search site’s rating to the copy page from external locations. The actual page is lower, and you can consider it as a duplicate.
Delete it from its database by a search engine. Any can use this method of hacking for maliciously delivering sites. Proxy hacking can allow users to steal account information from fake banks. Also, you can sell or use it to steal money from the bank account.
The intruder can also use the hack. As a result, this system leads the user to a website. That’s why ransomware infects this website to jeopardize their devices with several disasters.
Some ways to compromise proxy skills are available. For example, some owners of websites suspect a proxy hack. So, they will verify the hypothesis by looking for a term exclusive to the domain. Your search engine results page should appear (SERP). By the way, it could be a proxy page if a second site of the same contents appears.
How to connect a proxy with a Browser
Internet Explorer Settings
- Click Tools.
- Choose Internet Options.
- Select the Connections Tab.
- Click LAN settings.
- Select the box with the title “Use a proxy server for your LAN.”
- Choose the IP Address of the Server and the Port Number.
- After that, click OK.
The ways of firefox setting format
- Click the Firefox button.
- select Options
- Click Options
- Choose the Advanced Tab you find.
- Select Settings
- Click Manual Proxy Settings for the best result.
- In the HTTP Proxy pot, enter the IP Address of the Server then, click OK.
The ways of Google Chrome Settings
- Click the Customize and Control Button
- Choose under the Hood
- Make Change proxy settings
- Select LAN Settings
- Check the “Use a proxy server from your LAN” box
- Give the IP Address of the Server and the Port Number
- Click OK
Safari Settings
- Select Safari
- Choose Preferences
- Click Advanced
- Click Change Settings
- Check the Web Proxy pot
- G the IP Address of the Server and the Port serial
- after that, click Apply Now
What is a proxy – Proxy vs. VPN: Privacy
Due to privacy issues, 74% of Americans restricted their internet usage. Configured VPNs provide complete protection of your data from your server to your destination. This privacy ensures that spying on the data is even more challenging for people. The coding prevents your data from interception by hackers, even though you are on an open WIFI network.
As the VPN uses end-to-end encryption, you cannot access the data either on your ISP, firewall, staff, or government. For this cause, the Chinese government tries to limit access to VPNs by the public.
Because the ISP cannot snoop on the traffic, there is no way to verify whether you enter blocked websites. VPNs can also mask and difficulty distinguish your IP address and location from the website that you use. These servers function as an intermediary to hide your IP from the website you are visiting.
Also, with VPN or proxy, fingerprinting devices and the other technologies of scrupulous advertisers are still susceptible. As a result, displaying “appropriate” advertising is easy. Yet, you find it impossible for enterprises to connect the dots, at least by shielding your IP address.
What is a proxy – Proxy vs. VPN: Cookies
Legislation (like GDPR, CCPA, and more Internet privacy) has prompted many users. Fear using cookies by advertisers and blogs to trace all their activities. Conformity to GDPR is one of the EU business world’s latest hot topics. And for a good cause. And for a good reason.
According to this recent legislation, nearly every website tracking you by cookies has to request your approval. You have seen it hundreds of times on those prompts already. And here is the cookies thing. You can save and store them on your machine’s hard disk. Also, download cookies through the VPN to your user. But, for a VPN, the cookie errors with your own VPN’s IP address.
And it provides some degree of fingerprint protection and other digital monitoring techniques. This process often stores a cookie for another IP address on its website. Also, you must remove all cookies from your machine before you begin to use a VPN. Otherwise, existing cookies could interfere with the privacy layer added. The website will attach it to your source and IP address and use it to help fingerprint your device.
What is a proxy – The Pitfalls of Using Proxies
Companies are common to control and protect business networks by using proxies. Even so, the architects have developed representatives. These devices counter modern security risks or new technology. Also, these are handheld devices and the Internet. Proxies are no longer enough to protect a network or cloud connectivity today.
Proxies also have significant architectural faults. Besides, visibility-reduced proxies are stand-alone, independent products. These options serve only a select range of applications. Besides, the total network traffic is not entirely available. You cannot combine failure to integrate other safety goods Proxies.
You should learn policymaking or other network security capabilities. A separate antivirus program cannot factor in any malicious file or threats from an intrusion prevention device. That’s why proxies cannot check any data loss legally. Also, an organization does not permit you for any malware or greenlight traffic.
This pitfall could involve blind spotting and possible inspection holes. These setbacks are some sites, DNS, and FTP traffic for Office 365 or even traffic. Also, they were passing a proxy due to a ‘proxy friendly program. By the way, the representatives support a few Protocols, a few network protocols, including HTTP, HTTPS, FTP, and DNS.
They cannot differentiate between programs that move through or recognize different protocols. You can use any application for non-standard ports. Risks to defense some process bypasses end-user computers and conventional methods of URL. Leisure Proxy-based devices need robust computational infrastructure, fast processing, and high scalability. So that restricts their possible use. All this allows businesses to take a much more advanced security strategy than they have in the past.
Wrapping up with what is a proxy
A proxy server is an intermediary for our web requests. On the other hand, this server provides our web transactions with more anonymity. We proxy our JSONPlaceholder endpoint.
And rewrite our URL to keep our identity masked from the API with our Node.js sample. Though forward and reverse proxies can perform various purposes. This method can overall reduce safety threats. So, it improves confidentiality and also enhances the navigational pace.
Conclusive Discussion
Above all, we can hope that now you know all about what is a proxy. We tried and researched a lot to explain the whole thing simply and easily. If you have any questions, then feel free to knock us by the comment box. We will try to appreciate your queries.